Cisco Network Security Portfolio
Project Overview
This portfolio showcases a comprehensive enterprise network security implementation using Cisco Packet Tracer. The project demonstrates advanced networking concepts and security mechanisms that protect against various threats while ensuring high availability and performance.
The network is designed with a focus on security, redundancy, and scalability, making it suitable for medium to large enterprise environments. It incorporates industry best practices for network segmentation, access control, and threat mitigation.
Network Topology and Segmentation
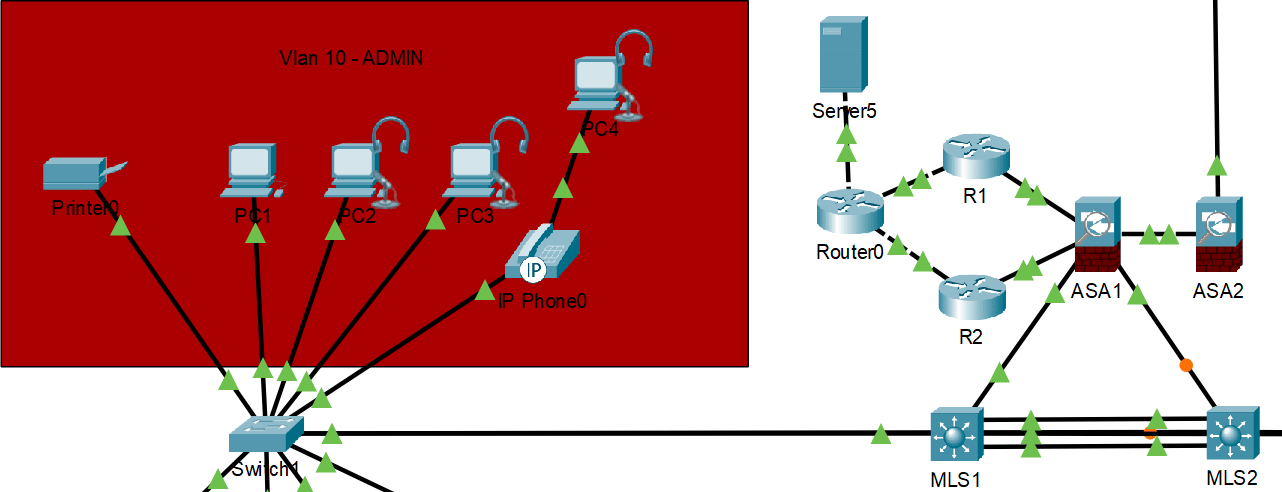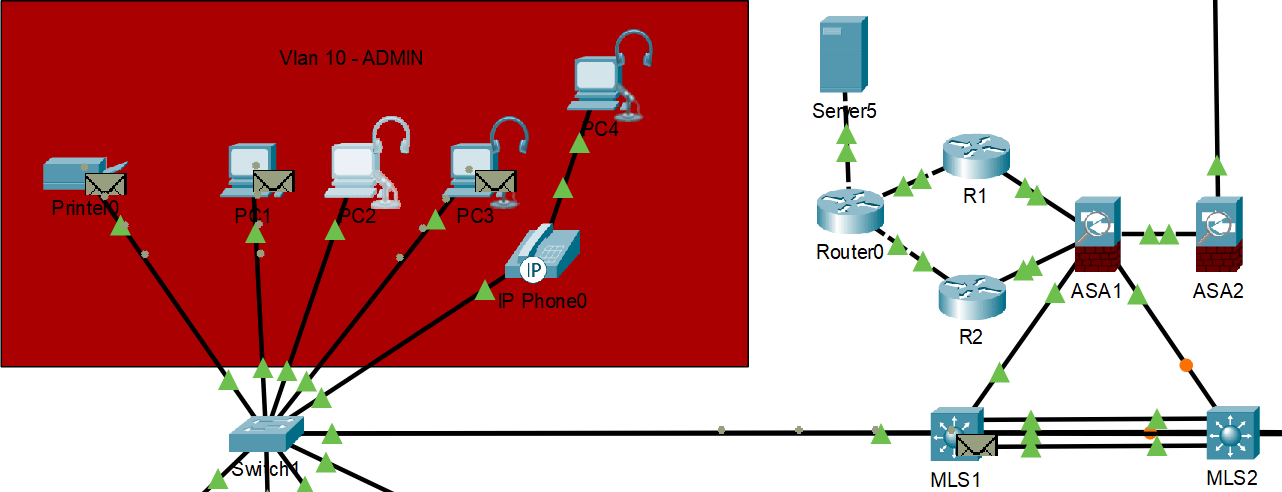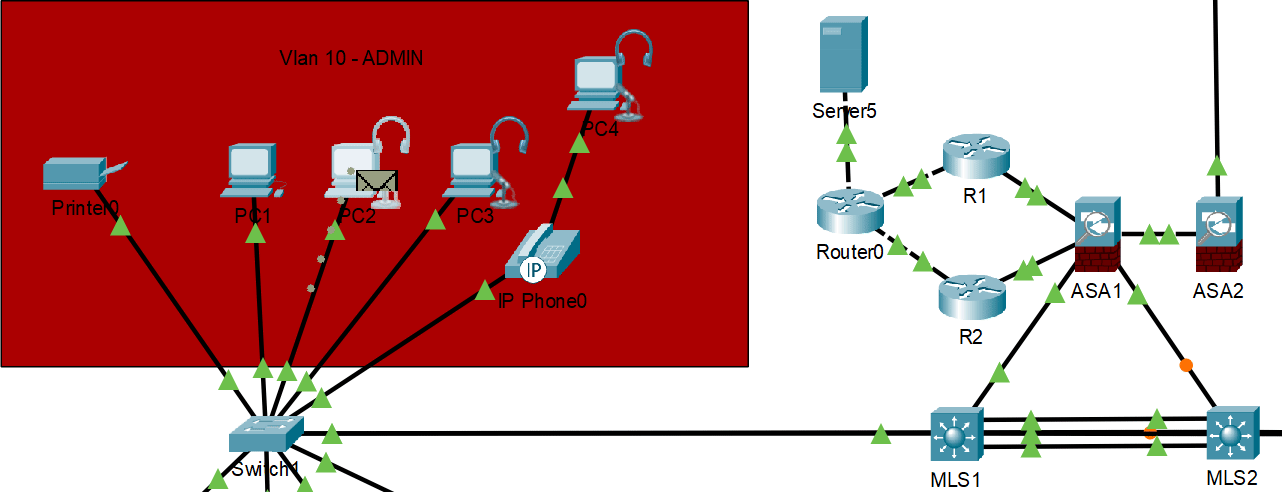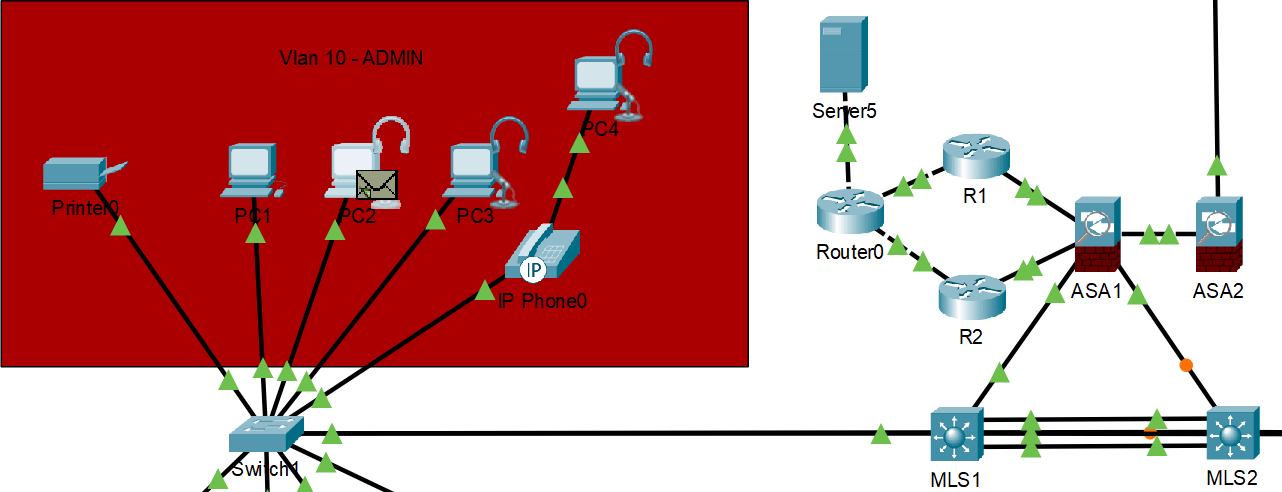
The network is built with a hierarchical design featuring core, distribution, and access layers. This architecture provides clear traffic flow paths, simplified troubleshooting, and enhanced security through isolation.
VLAN Segmentation
The network is divided into multiple VLANs to isolate different departments and services:
- VLAN 10: Administration
- VLAN 20: Finance
- VLAN 30: HR
- VLAN 40: Engineering
- VLAN 50: Guest Network
Inter-VLAN Routing
Implemented using multilayer switches (MLS1 and MLS2) that function as the distribution layer. These switches perform routing between VLANs while applying access control lists to restrict unauthorized traffic between segments.
DMZ Implementation
A demilitarized zone (DMZ) is configured to host public-facing services like web servers, ensuring they remain isolated from the internal network to prevent lateral movement in case of compromise.
Comprehensive Security Features
The network implements multiple layers of security controls to protect against both external and internal threats. These mechanisms work together to create a defense-in-depth strategy.
Access Control Lists (ACLs)
Extended ACLs are implemented on routers and multilayer switches to filter traffic based on source/destination addresses, protocols, and ports. This ensures that only authorized traffic flows between network segments.
Port Security
Configured on access switches to limit the number of MAC addresses per port and use sticky learning to prevent MAC address spoofing attacks and unauthorized device connections.
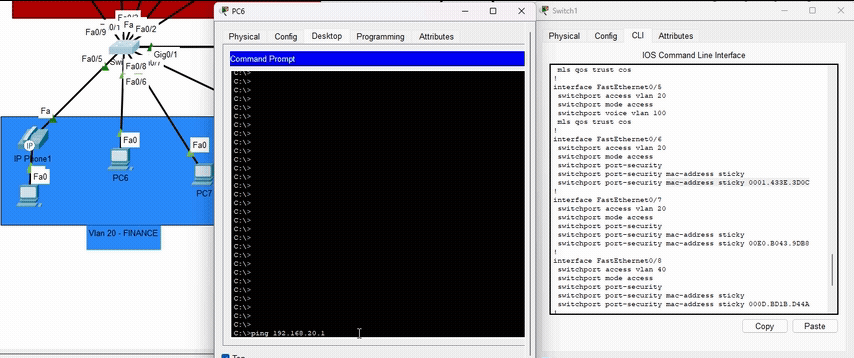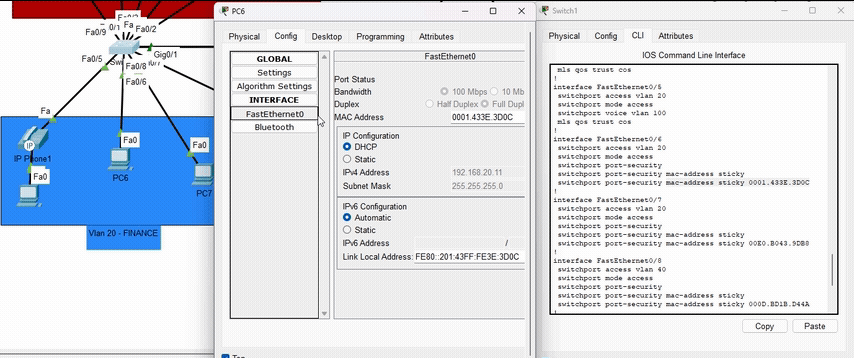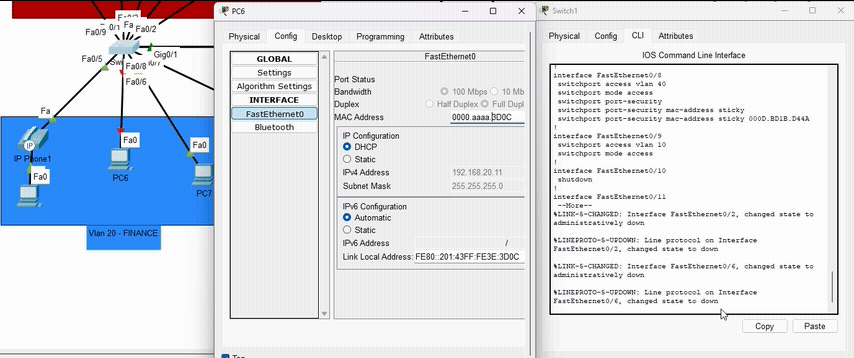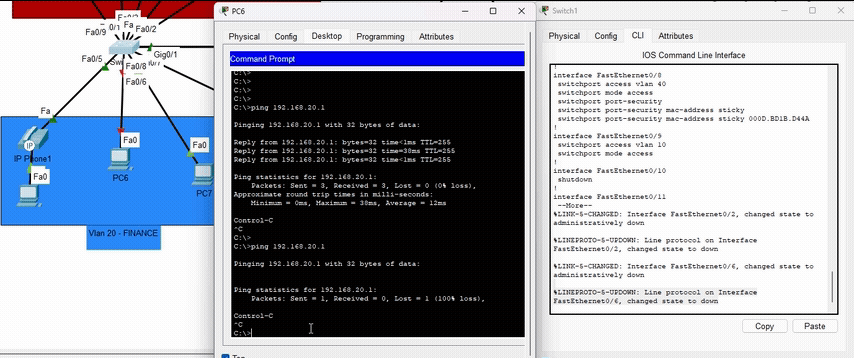
Demonstration of Port Security blocking unauthorized MAC addresses
DHCP Snooping
Implemented to prevent rogue DHCP server attacks by distinguishing between trusted and untrusted DHCP sources, protecting clients from receiving malicious IP configurations.
Dynamic ARP Inspection
Configured to prevent ARP spoofing attacks by validating ARP packets against the DHCP snooping binding database, ensuring that only legitimate ARP responses reach clients.
802.1X Authentication
Implemented for port-based network access control, requiring users to authenticate before gaining access to the network, preventing unauthorized connections.
Redundancy and High Availability
The network is designed with redundancy at multiple levels to eliminate single points of failure and ensure continuous operation even during hardware failures or maintenance.
Hot Standby Router Protocol (HSRP)
Implemented between MLS1 and MLS2 to provide gateway redundancy for all VLANs. This ensures that if one multilayer switch fails, the other takes over as the default gateway without disrupting network connectivity.
HSRP normal operation with primary gateway responding
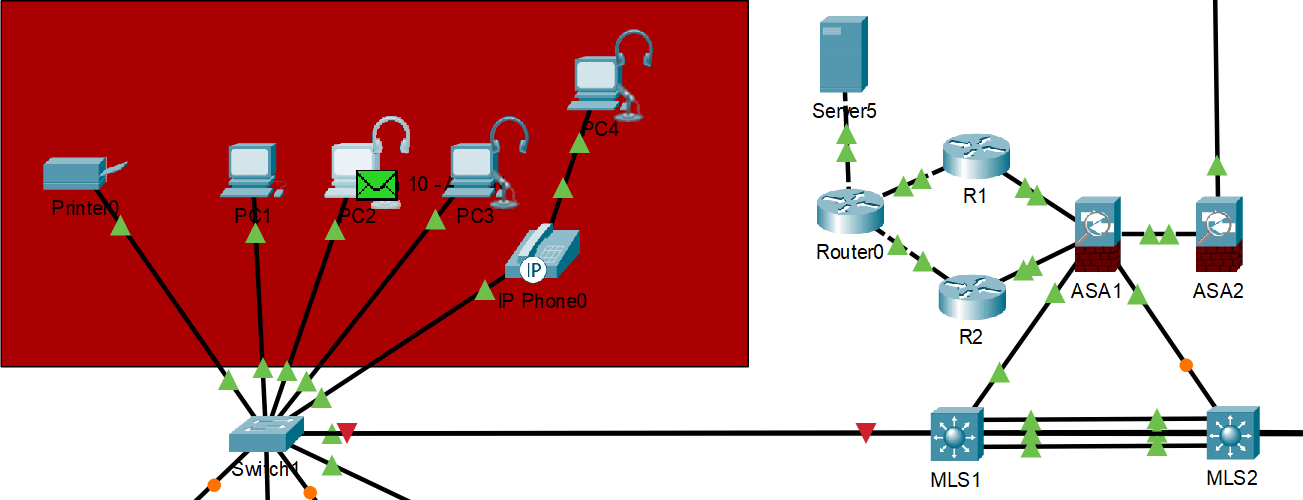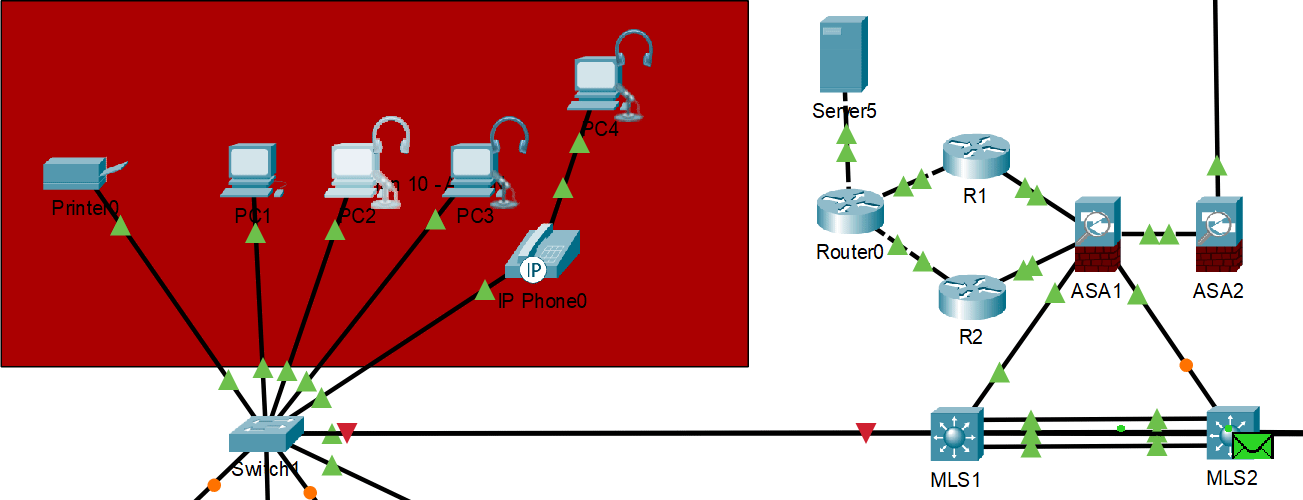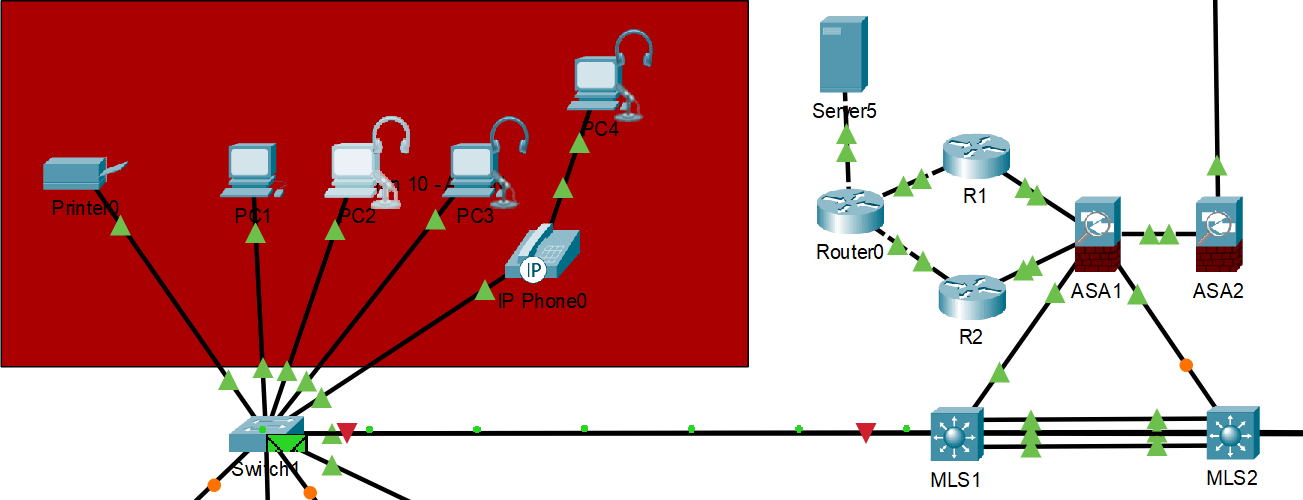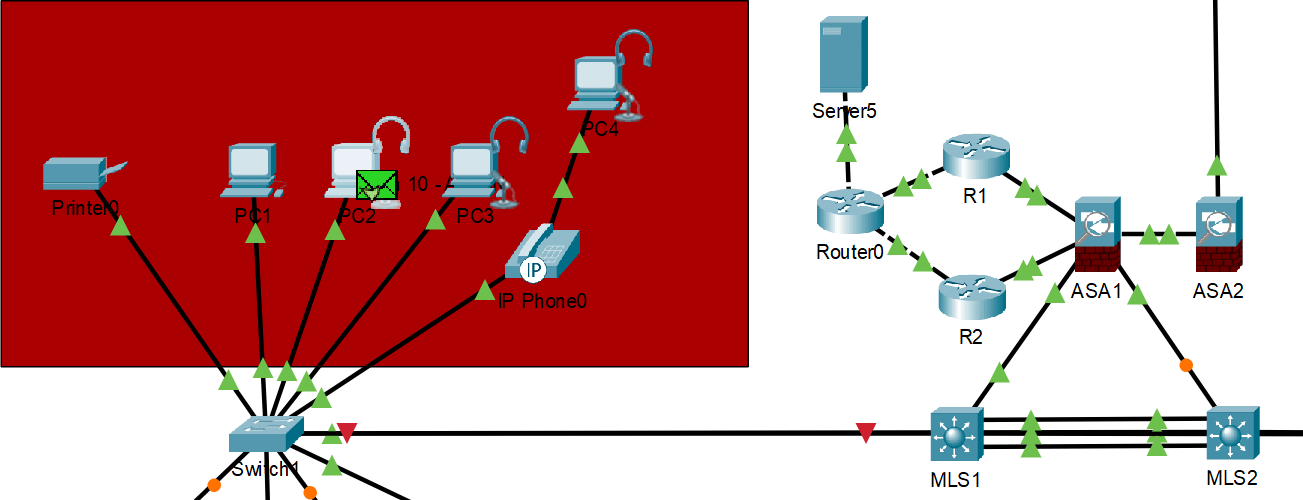
HSRP failover demonstration - backup gateway takes over when primary fails
EtherChannel
Multiple physical links are bundled into logical EtherChannel connections between switches, providing both increased bandwidth and link redundancy. If one link fails, traffic continues to flow through the remaining links.
Spanning Tree Protocol
Rapid PVST+ is configured to prevent switching loops while providing fast convergence in case of topology changes. Root guard and BPDU guard are enabled to protect the spanning tree topology from unauthorized modifications.
Feature Demonstrations
The portfolio includes demonstrations of key security and redundancy features in action, showing how they protect the network from various threats and ensure continuous operation.
The GIF animations above showcase:
- HSRP Failover: Demonstrating how network connectivity remains uninterrupted when the primary gateway fails
- Port Security: Showing how unauthorized devices are blocked when attempting to connect to the network
These demonstrations validate the effectiveness of the implemented security controls and high availability mechanisms in real-world scenarios.
Project Downloads
Download the complete Cisco Packet Tracer project file along with password documentation to explore the network configuration in detail.
Download Project Files